The introduction of 5G technology is reshaping the digital landscape, promising faster speeds, lower latency, and more reliable connectivity than ever before. With the potential to support millions of connected devices, 5G is set to power a new era of innovation in various sectors, from smart cities to autonomous vehicles. However, as with any technological advancement, 5G brings both opportunities and challenges — especially in the realm of cybersecurity.
In this blog post, we will delve into the impact of 5G on cybersecurity, exploring both the opportunities it presents for enhancing security and the challenges it introduces in terms of vulnerabilities and threats.
What Is 5G?
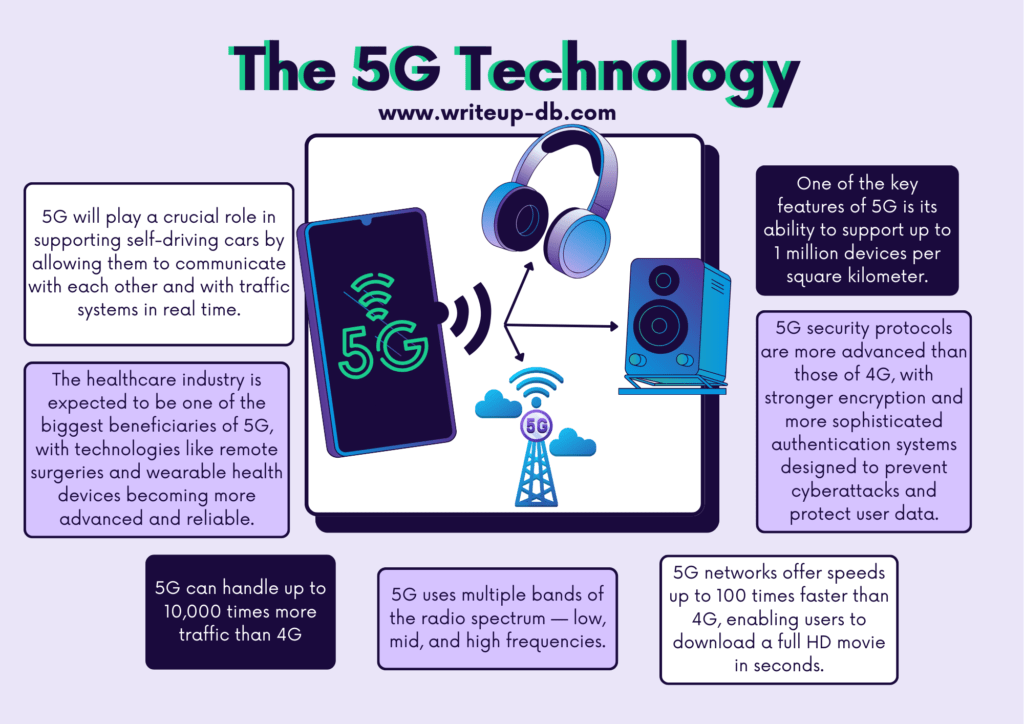
Before we dive into the impact on cybersecurity, it’s essential to understand what 5G is. In simple terms, 5G is the fifth generation of wireless communication technology. It offers significantly improved speeds and responsiveness compared to its predecessor, 4G. With 5G, users can experience data transfer rates as fast as 20 Gbps, ultra-low latency, and the ability to support up to 1 million devices per square kilometer. This makes 5G an essential building block for the Internet of Things (IoT), smart cities, and other data-heavy applications.
Opportunities Brought by 5G in Cybersecurity
1. Improved Security Protocols
5G networks are built with advanced encryption protocols, providing better protection against cyber threats. These networks use stronger encryption algorithms and offer enhanced authentication mechanisms, making it more challenging for attackers to eavesdrop on communications or impersonate devices.
Additionally, 5G introduces network slicing, which allows for the creation of isolated, virtual networks for specific use cases. This means that sensitive data, such as those used by emergency services or financial institutions, can be transmitted in isolated, secure “slices” of the network, reducing the risk of breaches.
2. Enhanced Network Monitoring and Detection
5G’s enhanced capabilities enable more effective real-time monitoring of network traffic. This allows cybersecurity professionals to detect and respond to threats faster than ever before. The increased bandwidth and speed offered by 5G can also improve the use of machine learning and artificial intelligence (AI) in detecting potential security threats. These technologies can analyze vast amounts of data in real time, identifying patterns that may indicate an attack, such as Distributed Denial of Service (DDoS) or ransomware campaigns.
3. The Potential for New Security Solutions
As 5G networks evolve, so too will the solutions that protect them. 5G will encourage the development of new, advanced security tools that can combat emerging threats. For example, edge computing — the practice of processing data closer to where it’s generated — is expected to play a significant role in securing 5G networks. By processing sensitive data closer to its source, edge computing reduces the need to transmit data over longer distances, limiting the exposure to potential attacks.
Moreover, 5G can drive the growth of blockchain technology, which can provide decentralized security solutions. Blockchain can help ensure data integrity, transparency, and traceability, offering a promising solution for secure transactions and communications in a 5G-powered world.
4. Supporting IoT Security
The increase in IoT devices supported by 5G opens up new opportunities for connected environments. Smart cities, connected vehicles, and healthcare devices will all benefit from 5G’s low latency and increased capacity. This also opens up opportunities for cybersecurity professionals to focus on securing IoT environments. Properly implementing strong encryption, authentication protocols, and security patches can help mitigate the risks posed by IoT vulnerabilities.
Challenges and Cybersecurity Risks of 5G
While 5G presents many exciting opportunities for cybersecurity improvements, it also introduces several new challenges that cannot be overlooked. The rapid expansion of 5G networks, the proliferation of connected devices, and the complexity of new infrastructure can create significant security risks.
1. Increased Attack Surface
One of the most significant challenges introduced by 5G is the expanded attack surface. With 5G’s ability to support billions of IoT devices, each connected device becomes a potential entry point for cyber attackers. Many IoT devices are designed with limited computing resources, making it difficult to implement robust security measures like encryption or firewalls. As a result, these devices may become vulnerable to attacks like malware infections or botnet hijacking.
The massive number of connections that 5G enables means that any vulnerability within an IoT device could serve as an access point for hackers to infiltrate an entire network. This could lead to widespread disruptions, data breaches, or worse, critical infrastructure failures.
2. Increased Complexity in Networks
The architecture of 5G networks is far more complex than previous generations, utilizing technologies such as virtualized networks, software-defined networking (SDN), and network function virtualization (NFV). This complexity introduces new potential vulnerabilities and makes securing the network more difficult.
Because 5G networks rely on many more interconnected systems and devices, there are more opportunities for misconfigurations or flaws that could be exploited by hackers. Moreover, managing security for such a dynamic and distributed network can pose significant challenges for cybersecurity teams, requiring them to adopt new strategies and tools to ensure comprehensive protection.
3. Supply Chain Vulnerabilities
As 5G networks rely heavily on hardware and software components from various suppliers, there is an inherent risk of supply chain vulnerabilities. Malicious actors could compromise network equipment during manufacturing or distribution, planting backdoors that could later be exploited.
Additionally, if the components used to build 5G infrastructure are not rigorously vetted for security, it could introduce weak points in the network that attackers could target. In this context, securing the 5G supply chain becomes a critical priority for telecom operators and governments alike.
4. Threats from Nation-State Actors
As 5G becomes critical infrastructure for governments and corporations, it is expected to become a prime target for nation-state actors. Countries may attempt to exploit weaknesses in 5G networks for espionage, disruption of critical services, or other malicious activities.
Nation-state-sponsored cyberattacks are often sophisticated and well-resourced, posing significant challenges for defenders. The geopolitical landscape of 5G, with debates over equipment from certain vendors, adds another layer of complexity. For instance, concerns over backdoors in network equipment from foreign manufacturers have led some countries to ban certain suppliers from participating in their 5G networks.
5. Privacy Concerns
The increased connectivity of 5G can potentially lead to privacy violations. With so many devices connected to the network and transmitting data, personal and sensitive information may be collected on an unprecedented scale. This data can be used by malicious actors for targeted attacks, or it could be misused by organizations for unethical surveillance practices.
Additionally, 5G networks may create challenges for data sovereignty. As data moves across borders more freely with 5G’s capabilities, countries will need to establish clear guidelines for how data is handled, stored, and shared to protect users’ privacy.
Addressing 5G Cybersecurity Challenges: What Needs to Be Done?
To fully realize the benefits of 5G while mitigating cybersecurity risks, several measures need to be taken by governments, organizations, and individuals:
- Adopt a Zero Trust Model: Zero trust is an approach to cybersecurity that assumes no user or device is inherently trusted. Adopting this model will be essential for securing 5G networks, especially given the increased complexity and number of devices connected. Every device and user must be continuously verified before accessing sensitive data or systems.
- Regular Security Audits: As 5G networks expand, regular security audits will become crucial in identifying vulnerabilities. These audits should cover every aspect of the network, from IoT devices to network infrastructure, to ensure that potential threats are mitigated early on.
- Collaboration Between Public and Private Sectors: Governments, telecom providers, and cybersecurity firms need to collaborate to ensure the security of 5G networks. Sharing threat intelligence and working together on setting standards can help create a more secure 5G ecosystem.
- Strong Supply Chain Security: Ensuring that all components used in 5G networks come from trusted sources is critical. Rigorous testing of equipment for security flaws, as well as establishing strong relationships with trusted suppliers, can help mitigate supply chain risks.
- User Awareness and Education: Users must be educated on the importance of securing their devices in a 5G-powered world. This includes regular software updates, enabling security features such as multi-factor authentication, and being vigilant against phishing attacks.
Conclusion
5G is an exciting development with the potential to transform the way we live and work. However, its vast opportunities come with new and evolving cybersecurity challenges. The increased attack surface, network complexity, and potential privacy concerns require a proactive approach to securing 5G infrastructure. Governments, organizations, and individuals must work together to implement robust security measures that protect against emerging threats and ensure the safe deployment of 5G technology.
As we move into the 5G era, staying informed and prepared will be crucial to ensuring that this transformative technology is both a boon for connectivity and secure for users worldwide.
